The Neodyme Blog


Diving into the depths of Widevine L3

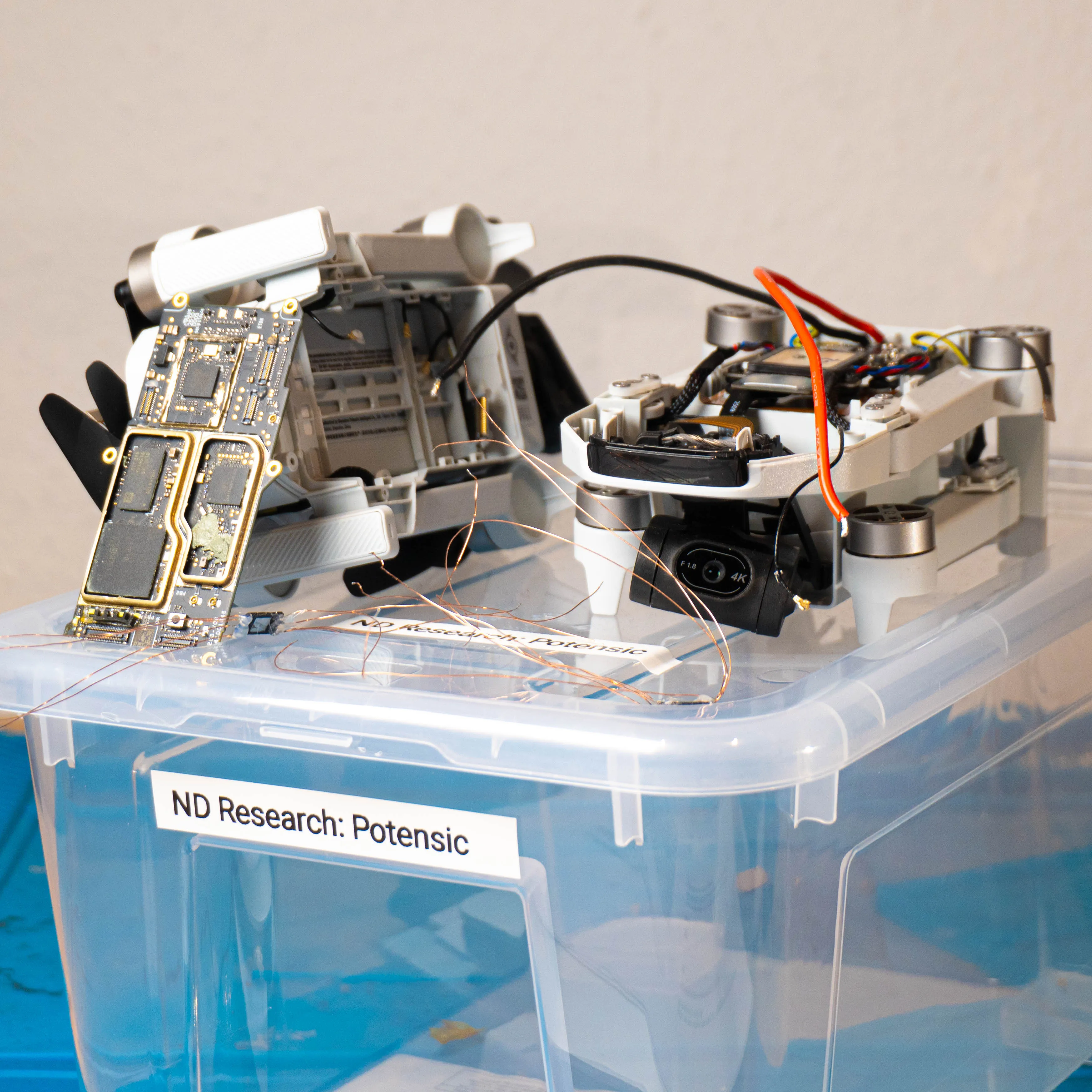
Pwn2Own Ireland 2024: QNAP Qhora-322

Lenovo DCC: Part 1 - A simple ACL Exploit

Building Our Own Post-Quantum FIDO Token

Did You Train on My Voice? Exploring Privacy Risks in ASR

Your router might be a security nightmare: Tales from Pwn2Own Toronto 2022

Riverguard: Mutation Rules for Finding Vulnerabilities
Pwn2Own Ireland 2024: Canon imageCLASS MF656Cdw
HTML to PDF Renderer: A tale of local file access and shellcode execution

The Key to COMpromise - Writing to the Registry (again), Part 4

The Key to COMpromise - Downloading a SYSTEM shell, Part 3
Introducing HyperHook: A harnessing framework for Nyx

The Key to COMpromise - Abusing a TOCTOU race to gain SYSTEM, Part 2

Windows BitLocker -- Screwed without a Screwdriver

On Secure Boot, TPMs, SBAT, and downgrades -- Why Microsoft hasn't fixed BitLocker yet

The Key to COMpromise - Pwning AVs and EDRs by Hijacking COM Interfaces, Part 1

Solana Consensus - From Forks to Finality

From Guardian to Gateway: The Hidden Risks of EDR Vulnerabilities
