CVE-2025-1865 ‒ Local Privilege Escalation in Virtual CloneDrive Kernel Driver
Description
Virtual CloneDrive allows users to mount ISO files and other disk image formats as virtual drives on their computer.
Its kernel driver, accessible to low-privileged users, exposes a function that fails to properly validate the privileges of the calling process.
This allows creating files at arbitrary locations with full user control, ultimately allowing for privilege escalation to SYSTEM.
Vulnerability
The dissambled code of the vulnerable function looked as follows:
00012b10 NTSTATUS create_device_function(int64_t* input_buffer, void** output_buffer)
00012b2e *(input_buffer + 0x121) = 000012b3c void* FileHandle = nullptr00012b40 int16_t device_path_ansi00012b40 RtlInitAnsiString(&device_path_ansi, input_buffer)00012b4000012b58 if (device_path_ansi u<= 8 || *input_buffer != 0x5c6563697665445c) // "\Device\"00012b5a return STATUS_INVALID_PARAMETER00012b5a00012b6e int64_t AllocateDestinationString00012b6e AllocateDestinationString.b = 100012b71 void device_path_unicode00012b71 NTSTATUS ntstatus = RtlAnsiStringToUnicodeString(&device_path_unicode, &device_path_ansi, AllocateDestinationString)00012b7100012b79 if (ntstatus s< STATUS_SUCCESS)00012c47 return ntstatus00012c4700012ba3 OBJECT_ATTRIBUTES ObjectAttributes00012ba3 ObjectAttributes.ObjectName = &device_path_unicode00012bc0 ObjectAttributes.Length = 0x3000012bd5 ObjectAttributes.RootDirectory = 000012be7 ObjectAttributes.Attributes = 0x4000012bf6 ObjectAttributes.SecurityDescriptor = 000012bfe ObjectAttributes.SecurityQualityOfService = 000012c0b void IoStatusBlock00012c0b NTSTATUS status_zwcreatefile = ZwCreateFile(&FileHandle, DesiredAccess: *(input_buffer + 0x122), &ObjectAttributes, &IoStatusBlock, AllocationSize: nullptr, FileAttributes: *(input_buffer + 0x132), ShareAccess: *(input_buffer + 0x126), CreateDisposition: *(input_buffer + 0x12a), CreateOptions: *(input_buffer + 0x12e), EaBuffer: nullptr, EaLength: 0) // vulnerable function call00012c18 RtlFreeUnicodeString(UnicodeString: &device_path_unicode)00012c23 *output_buffer = FileHandle00012c26 return status_zwcreatefileThis function is invoked using the IOCTL 0x22e08b and does not set the OBJ_FORCE_ACCESS_CHECK flag, when calling ZwCreatFile.
Furthermore, the process calling the function controls the file path.
With this, it is possible to create an arbitrary file from the kernel.
For this file the user invoking the kernel driver gets full access rights:
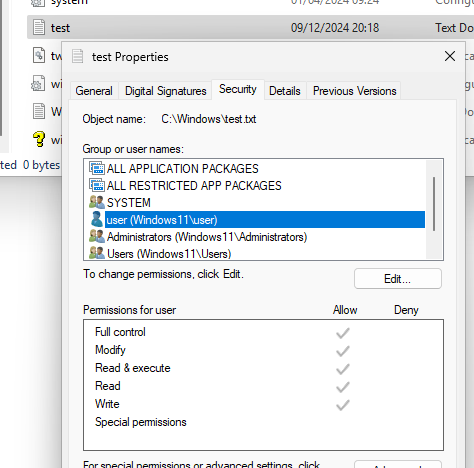
This can be abused to gain SYSTEM privileges.
Mitigations
Install a current version of Virtual CloneDrive. The vulnerability was fixed in version 5.5.3.0.
Timeline
| Date | Action |
|---|---|
| 14.12.2024 | Initial contact with vendor about the vulnerability |
| 20.12.2024 | Neodyme provides more details concerning the vulnerability |
| 07.01.2025 | Update from vendor that the issue could be reproduced successfully and will be addressed |
| 16.02.2025 | Neodyme receives a fixed version for testing |
| 18.02.2025 | Neodyme confirms that the exploit does no longer work in the fixed version |